Common CSRF Pitfalls
Because Ory Hydra isn't just an API, but instead talks to your users' browsers directly, several security measures have been implemented in Ory Kratos. One of them is protection against CSRF:
CSRF is an attack that tricks the victim into submitting a malicious request. It inherits the identity and privileges of the victim to perform an undesired function on the victim’s behalf. For most sites, browser requests automatically include any credentials associated with the site, such as the user’s session cookie, IP address, Windows domain credentials, and so forth. Therefore, if the user is authenticated to the site, the site will have no way to distinguish between the forged request sent by the victim and a legitimate request sent by the victim.
Common Pitfalls
Sometimes, cookies and CSRF just wont work - all requests end up with a 401 Unauthorized or 400 Bad Request. Here are some common causes and easy fixes if that happens to you!
Before starting to debug cookie and CSRF issues, make sure to check out the Chrome Developer Tools (or any comparable technology) Cookies tabs in the Application tab
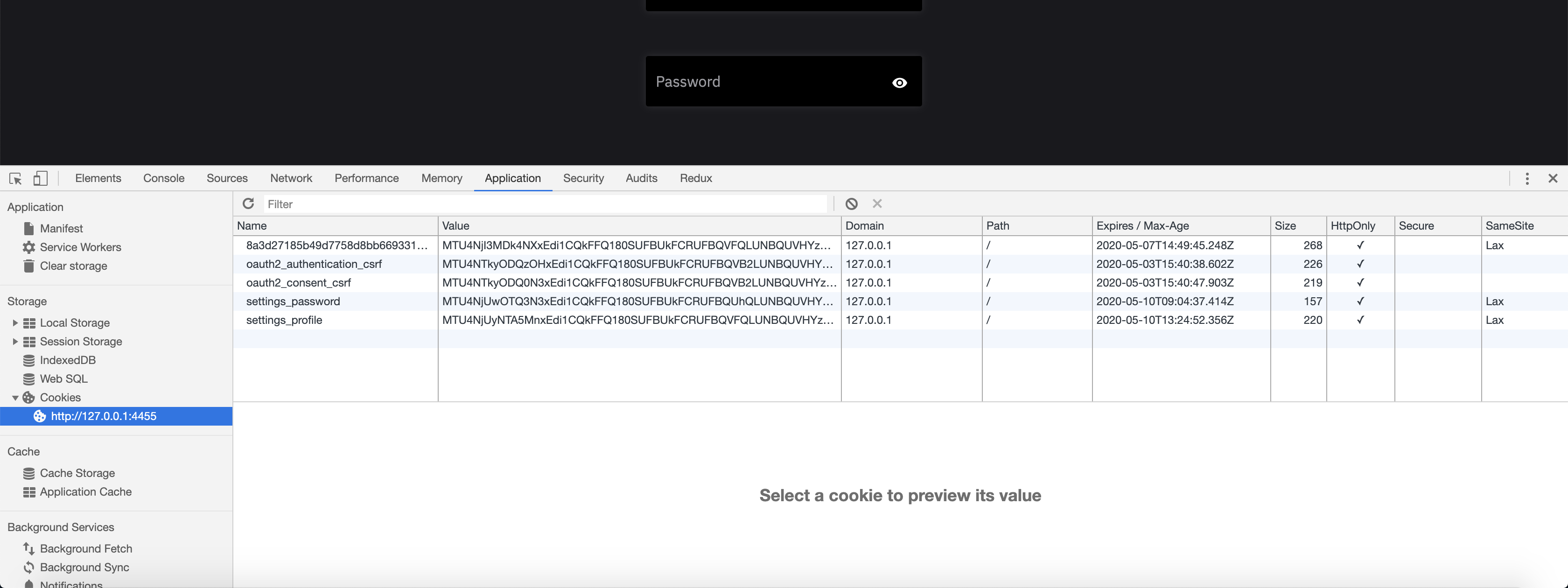
as well as the network tab - look for Cookie and Set-Cookie HTTP Headers:
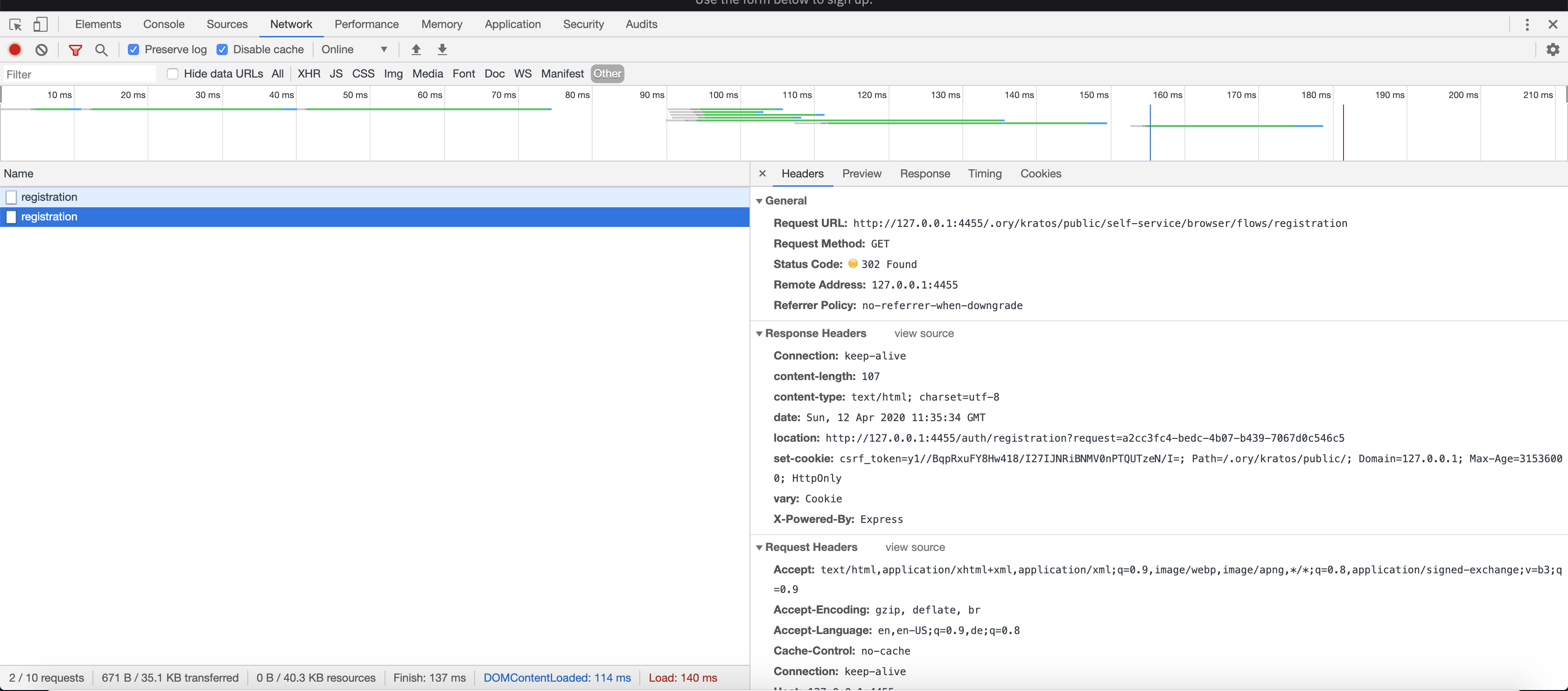
Same-Site in Chrome
Google Chrome changed the behavior of SameSite=None so that it isn't possible
to use this SameSite mode without the HTTP Cookie secure flag.
If you run a version of Ory Hydra 1.6 and below and experience this issue:
- Make sure to not use the
--dangerous-force-httpflag - Set configuration value
serve.cookies.same_site_modeor environment variableSERVE_COOKIES_SAME_SITE_MODEtoLax- this happens automatically for Ory Hydra v1.7.0 when running in HTTP mode.
Chrome rejects cookies without the secure flag if a cookie with the same name
for the same scope (domain, path) is set that has the secure flag. Ory Hydra
1.7.0+ uses different names for cookies with and without secure flag. For
versions prior to that, you need to delete the cookies for the domain in order
to get them working again.
Ory Hydra Running Over HTTP Without dev-mode Enabled
You are running Ory Hydra via HTTP but are missing the --dangerous-force-http
CLI flag:
hydra serve all -c path/to/config.yml --dangerous-force-http
Mixing up 127.0.0.1 and localhost
Use either 127.0.0.1 or localhost - so either IPs or hostnames - throughout
your flow because cookies from an IP aren't available to the hostname and
vice-versa.
Reverse Proxy / Load Balancers
You are running Ory Hydra behind a reverse proxy that strips the Cookie header. If the reverse proxy supports path rewrites that might also cause issues!
Running Flows in Separate Browsers or Browser Windows
You are running the OAuth2 flow in separate browsers, or in a browser with incognito mode. The Brave browser is also known for notoriously discarding cookies when used in "No-Tracking" mode.
Running Multiple OAuth2 Flows Simultaneously
You are trying to do two OAuth2 flows at the same time in the same Browser.
Cookie Same-Site Mode
You have changed the Cookie SameSite behavior. If this is the default value (you didn't change it), this shouldn't be an issue.
Using AJAX to call /oauth2/auth
You can't call /oauth2/auth using an AJAX request. It isn't allowed and
not possible with OAuth2. This endpoint can only be accessed using a normal
browser request by clicking a link or redirecting the end-user's browser to that
endpoint.